The US federal government and its international partners have made a significant new resource available to the cyber security industry. The new guidance of CISA and the Australian Cyber Security Center of the Australian Signals (ASDS ACSC), “Implementation of Siem and Soar platforms“ Offers a implementable assessment of the safety automatic landscape and the challenges that modern safety operating centers (SOCs) face.
The report offers a clear definition of a security orchestration, automation and reaction (soar). According to the instructions, “Automated a soar some of the answer to recognized cyber security events and incidents … by using predefined” playbooks “… These automated actions do not replace human residents, but can complement them.”
This guide confirms what security experts have experienced for years: Soar platforms of providers such as Splunk, Swimlane and Palo Alto Xsoar are not “set and forgetting” tools. These are platforms that require intensive, continuous configuration and maintenance to function, a fact that underlines the restrictions of a approach controlled by Playbooks.
The restrictions of Soar Playbooks and the rise of the ASOC
The core challenges described in the CISA report, from the hidden costs of Siem/Soar to the operational resistance of false positive aspects, are rooted in this dependence on static playbooks. Safety instructions such as effectively meet Essential eight Or cisa Cybersecurity performance goals (CPGs)A new approach is required. Here a new category of SoC automation comes into play. The next step in the development of traditional soar to an autonomous Sooc (ASOC) solution like the Morpheus of D3.
- Traditional soar rationalizes tasks by performing the play books that your team builds. The responsibility for examinations, correlations and the maintenance of these game books remains with your analysts.
- Morpheus ASOC automates the workload between Tier 1 and Tier 2. It creates autonomously dynamic, context -related answers (playbooks) based on the unique attributes of all warning and incidents. This eliminates the stress on the play book and provides more effects by completely examining every warning.
- Morpheus acts as AI-Copilot and offers incoming, cross-stack examinations, timelins for miter, link analysis and automated workflows for renovation and proactive threat hunting for animal-3 analysts who are responsible for the reaction and/or the provision of MDR (managed detection and response).
| CISA/ACSC identified challenge | The soar approach | The Morpheus Asoc solution |
| Inaccurate alarm and false positive results | Teams are often “surgically overwhelmed by false warnings” or they miss real incidents due to ineffective warning rules. | Filter noise before it reaches analysts. Morpheus is an asoc product that was developed for autonomous enrichment, correlation and prioritization of warnings in scale, which means that false and benign positive people are “filtered” from the queue. |
| Spielbuchtungsenchenkt | If the staff demands that the Personal Playbooks continuously adapts and tests as a change in the network and the threat landscape – an intensive and infinite process. | Self -generating, adaptive playbooks. Autonomously creates a unique investigation and reaction workflow for any warning that is tailored to its security stack and the specific threat and eliminates manual maintenance. |
| Risk inappropriate measures | An important technical challenge is to ensure that a Soar “does not take any measures against regular network activities” or hinders the responders, which can “significantly disrupt the provision of services”. | Offers AI-controlled studies with the governance of people in the loop. Morpheus coincides with her guidelines and calls on your team with a click before performing critical renovation steps to ensure full control. |
| Complex, costly implementation | A proper soar implementation includes considerable preliminary and persistent costs, from data reinforcement fees to the storage of employees with “sought-after, specialized skills”. | Offers value in days, not in quarter. Morpheus sits on her existing tools with over 800 integrations. It works on warnings and no protocols that can help reduce the data costs associated with conventional Siem/Soar tools. |
AI speed with human control: solving the dilemma “appropriate action”
The CISA guideline correctly identifies one of the greatest automation risks: Make sure that the Soar only took appropriate measures in response to actual cyber security incidents. An automated process that misinterprets an event can lead to considerable corporate disorders.
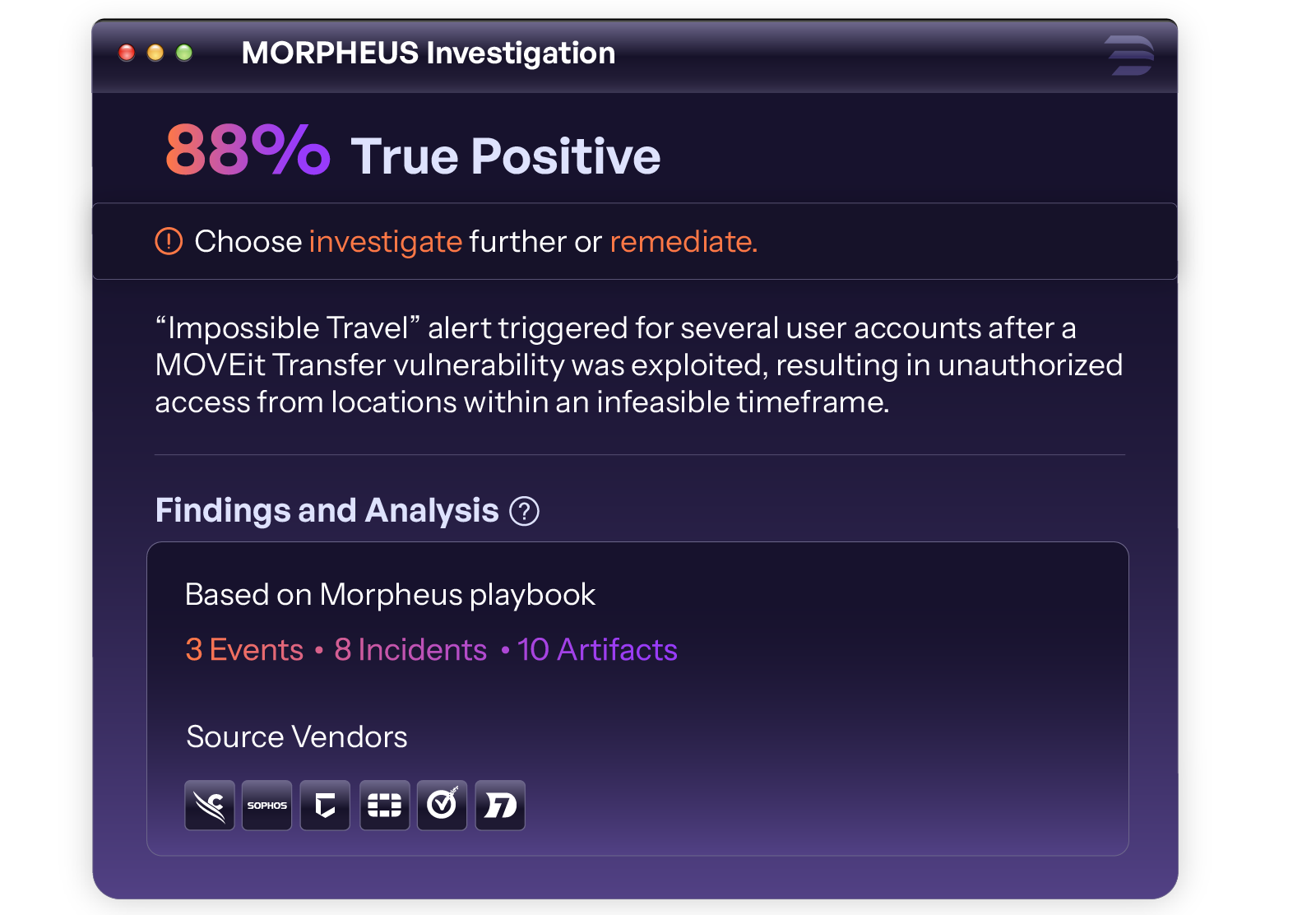
Here the ASOC model demonstrates its value. Morpheus is designed in such a way that they convey the speed of the AI with the certainty of human observation:
- AI-controlled recommendations: For each confirmed threat, Morpheus creates clear summaries, implementable next steps and a triage score in full stack to inform the answer.
- Entry requests with one click: Entry requests: For critical actions such as isolating a host or revocation of login information, Morpheus pauses and waits for an analyst to give the homepage.
- Complete transparency: All AI-generated logic are shown in Open Yaml, and every decision can be checked, changed and tested to ensure that your team retains complete control.
CISA's recommendations for Soar implementation offer a clear direction for the future of security automation. The time and resources to invest in the maintenance of brittle play books is no longer the most effective strategy. The logical next step is to achieve a more intelligent, more autonomous approach. Are you ready to explore the next development of security automation? Book a demo to see Morpheus in action. 
The new soar instruction from Post Cisa shows where automation must appear next in D3 Security.
*** This is a D3 Security blog written by Shriram Sharma, which was written by D3 Security. Read the original post at: https://d3security.com/blog/cisa-so-soar-Guidance-soc-automation/


